A meaningful result is an essential part of a thorough security analysis. The majority of pentest result reports focus on the identified vulnerabilities. Here's the problem: The scope of the tested environment is not apparent from this and is not comprehensible for you. That's not sufficient for us.

"It is important to us not only to perform qualitative analyses, but also to provide you with detailed documentation of the tests performed. With our test reports, we make our analyses transparent and demonstrate our quality standards. In 2021, we have taken our reporting to the next level."
Stephan Neumann
Head of usd HeroLab
We provide transparency for you in our test report
As demand for pentests increases, there are also an increasing number of providers competing, which makes it difficult for companies to evaluate differences in the quality of pentests ideally before a contract is signed. This is because the conducting of the actual pentest remains a black box from the client's point of view:
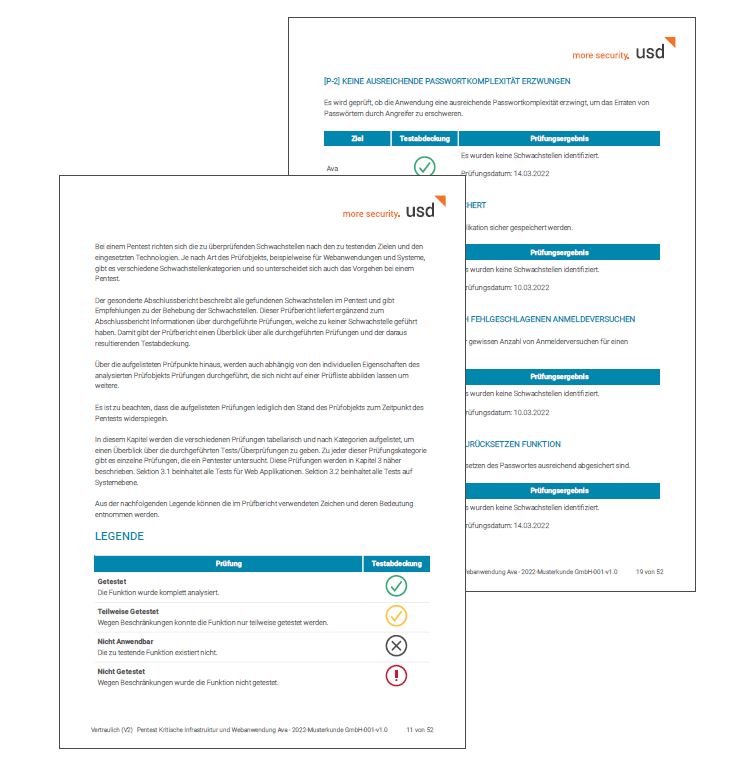
A final report merely documents which vulnerabilities were identified during the pentest. The report does not contain any information about whether and to what extent a function was tested. Our test report creates more transparency: It is an additional document that summarizes the scope as well as the result of the analysis. Here, we show which attack vectors were tested in connection with which functions and with what result - even if no vulnerability was identified there. This gives you greater transparency and allows you to evaluate the quality of our analysis.
Comprehensible pentest results
The best security analysis does not provide any benefit if the findings are not presented in a comprehensible and well-structured manner and not included concrete recommended measures. This is why we have fundamentally revised our pentest results reports and added a lot of useful information. By categorizing findings, for example, it is possible to identify fundamental issues. For example, many findings in "handling user data" within a web application indicate a lack of awareness of injection attacks among developers. Overall, we have revised the structure and presentation of the findings in our report and added internal references to improve legibility.
Reporting customized to your needs
The results of the technical analysis lead to extensive subsequent measures at your company:
- The results have to be processed further within the company
- Task have to be assigned to the right persons
- Remediation measures must be implemented, tracked and documented
Many companies use their own systems for this, for example based on Jira. For this purpose, we can easily provide a tabular summary of the results in a suitable import format. If requested, we can also use the company's own templates for the documentation of pentest results.
Are you interested in a pentest or do you need support?
Please do not hesitate to contact us.



