Information security is first and foremost about protecting your corporate assets. In our mini-series, we explain the terms, concepts and interesting facts about information security management in companies.
Part 1: The basics
Part 2: The ISMS in the company
Part 4: Enterprise Risk Management
What are vulnerabilities?
In the context of information security management, a vulnerability is a security gap in an organisation's IT systems. Companies can suffer damage if attackers exploit these vulnerabilities, for example by accessing IT systems and stealing or manipulating company data. If vulnerabilities remain undetected or are improperly handled, they can have consequences that threaten a company's existence.
With the help of an information security management system (ISMS), companies can organise their handling of vulnerabilities through defined processes and rules. Thus, vulnerabilities are usually identified in risk management and dealt with according to a previously defined methodology. In addition to the early detection of security vulnerabilities, the goal is to strengthen and improve the protection of corporate assets.
| Vulnerability |
| Insufficient protection of buildings |
| Insufficient access controls |
| Unencrypted information |
| Software vulnerability |
What are threats?
Threats are causes of an unwanted incident that could harm an organisation. Threats exist permanently and can exploit undetected or inadequately addressed vulnerabilities in a company to its disadvantage. A list of typical threats can be found in the annex of ISO/IEC 27005:2018. According to the BSI definition, threats that exploit a vulnerability become hazards. A publicly available overview of elementary threats can be found in the IT-Grundschutz-Kompendium.
Not every vulnerability is necessarily relevant to every type of threat. For example, an application that is not accessible via the Internet may have a vulnerability. However, due to the lack of external accessibility, this does not create a risk from external attackers, as the vulnerability cannot be exploited by them. Even vulnerabilities that cannot be exploited by current threats should, however, be documented by the company so that it can react promptly to new threats.
| Vulnerability | Potential threat |
| Insufficient protection of buildings | Theft |
| Insufficient access controls | Willful damage |
| Unencrypted information | Information theft |
| Software vulnerability | Unauthorised access by third parties |
What are risks?
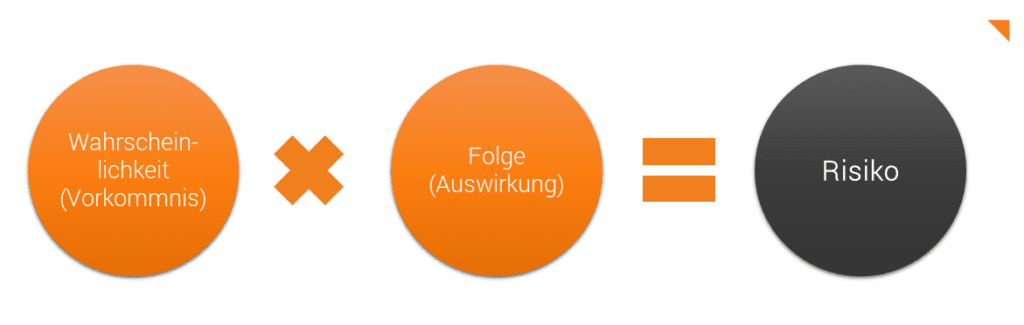
A risk arises when a threat encounters the vulnerability of an asset and negatively affects the information security of that asset. In information security, risks potentially cause the loss of key protection objectives. Risks are usually identified, analysed, assessed and dealt with in an information security risk management process. A prerequisite for the identification of risks is the prior identification of assets, vulnerabilities and threats. Risks cannot be fully assessed if data is incomplete.
Risks can be assigned to known assets by identifying their vulnerabilities and threats. Using systematic approaches, these risks are assessed in the risk analysis and examined for their probability of occurrence and potential impact. Based on this assessment, risk mitigation measures are defined, if necessary. The result of these steps is a list of risks that includes the respective risk owners, the risk assessments and the resulting measures. Based on the risk assessment, vulnerabilities can be prioritised according to their criticality.