The digital transformation in the financial sector has created new areas of attack for cyber criminals and therefore significant risks for...
INFORMATIONSSICHERHEIT
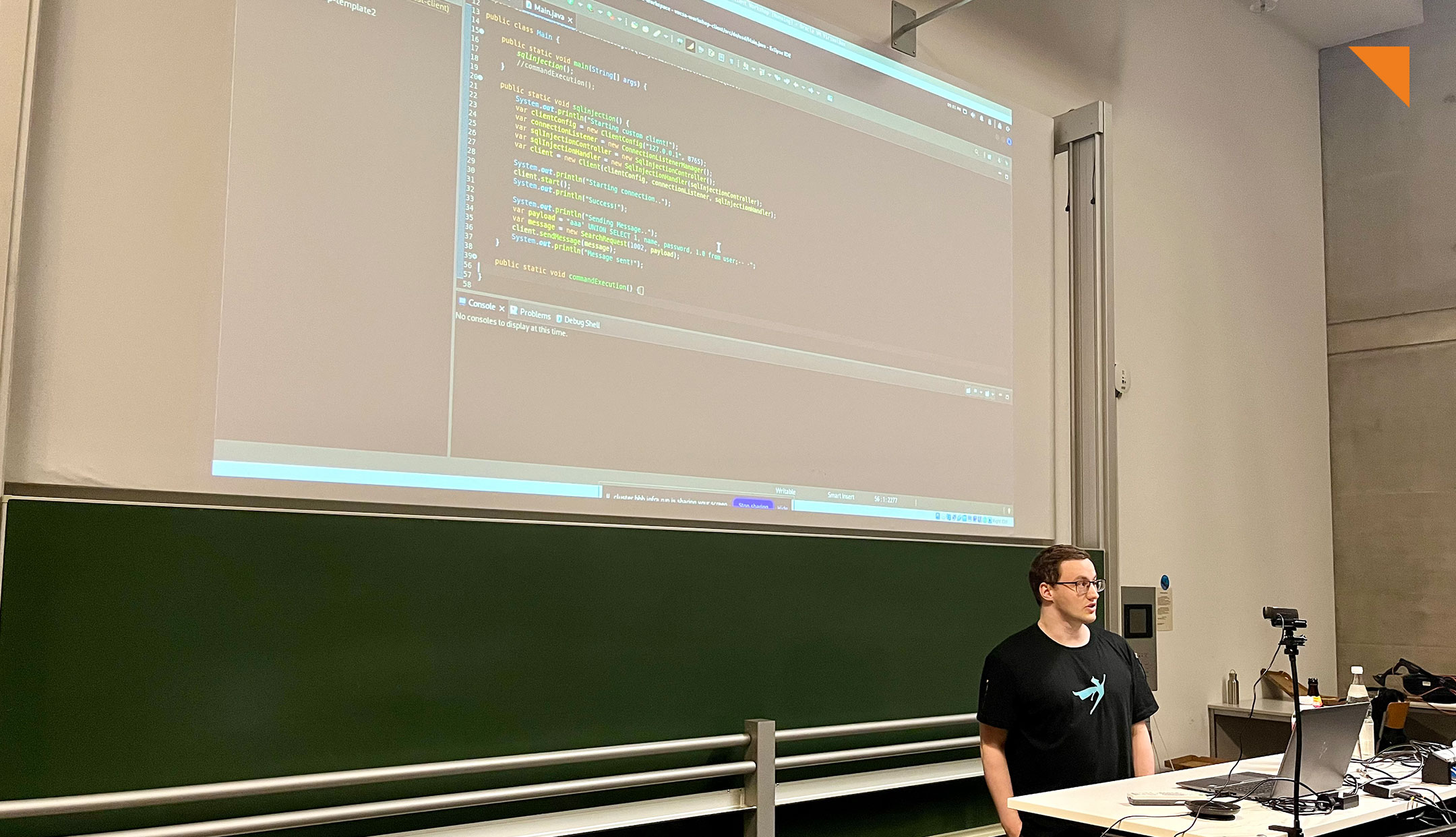
Fat Client Pentesting: Hands-On Decompilation & Exploitation - Guest Lecture at Hochschule München University of Applied Sciences
Last Tuesday, usd visited the Hochschule München University of Applied Sciences for the second time as part of the "IT Security" lecture series. Our...
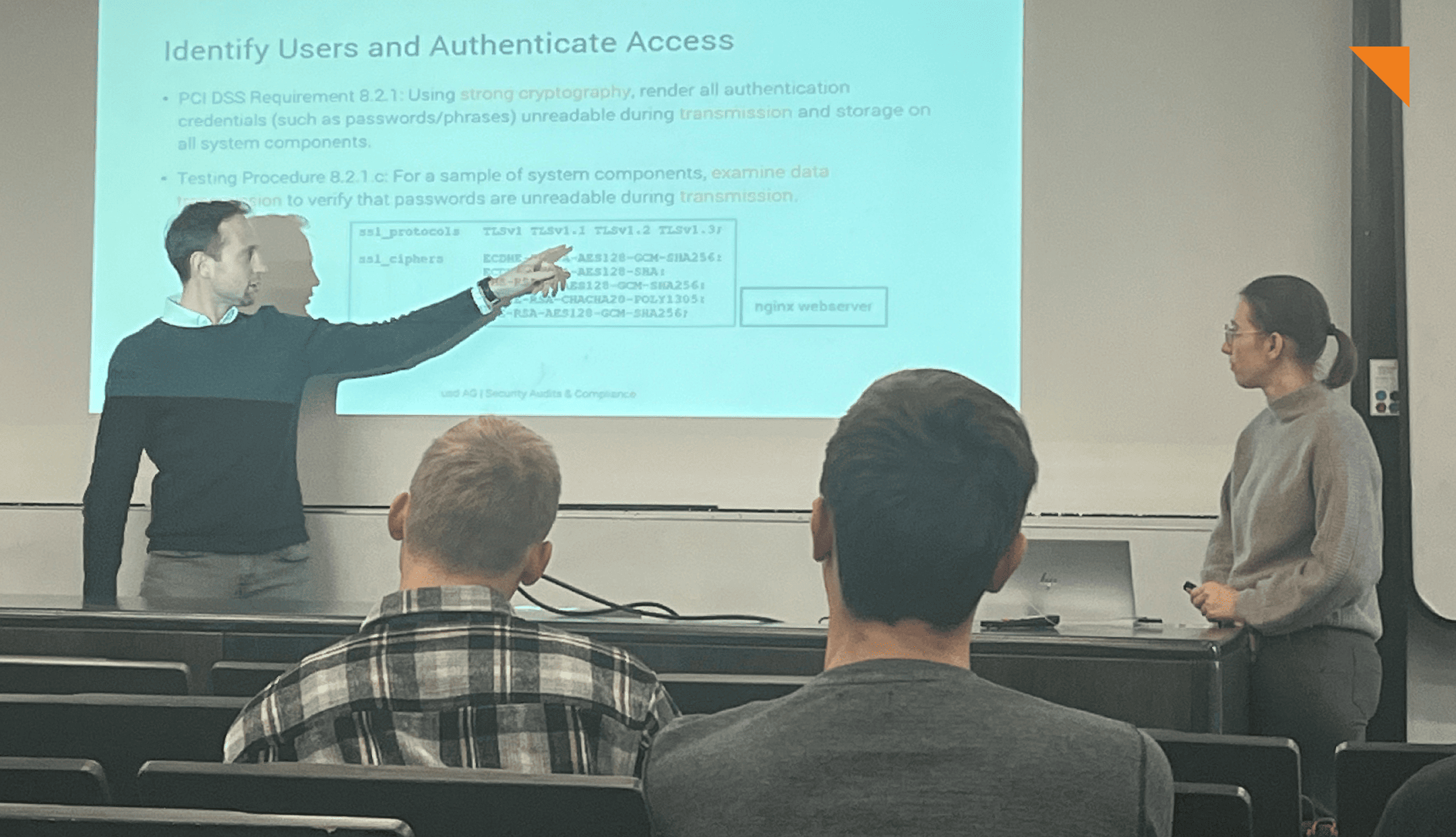
Guest Lecture at the TU Munich: Practical Insights into Cyber Security Audits and Compliance
Many people don't realize how much influence cyber security standards have on our daily lives. The credit card security standard PCI DSS is a great...
IT-GRC Congress 2023: usd Experts to Give Presentations
On November 7 and 8, 2023, ISACA Germany Chapter and dpunkt.verlag GmbH will host the IT-GRC Congress in Munich. Once again, the agenda of the...
Eurowings GmbH Achieves ISO/IEC 27001:2013 and PCI DSS Certifications with Support from usd AG
As for many companies in the aviation industry, the summer of 2022 was marked by extreme challenges for Eurowings GmbH: the pandemic, the tense...
Cyber Security Check: The 7 most important questions
Cyber security has become a key concern for businesses of all sizes in today's interconnected world, where organizations are increasingly reliant on...
Ready for the Future: usd PCI DSS Policy Templates Version 4.0 Now Available
Companies that store, transmit or process credit card data are required by requirement 12.1 of the Payment Card Industry Data Security Standard (PCI...
Internal audits according to ISO 27001 - Insights, tips and frequently asked questions
For many companies, preparing for ISO/IEC 27001:2022 (ISO 27001) certification is a major effort. But all the information security management system...
Cyber Security Insights: usd AG Holds Guest Lecture at Paderborn University
On April 25, 2023, Jan Kemper, Head of Security Audits at usd AG, held a guest lecture at Paderborn University. As part of the lecture Methods of...
PHOENIX group establishes Europe-wide ISMS with support from usd AG
Particularly in high-growth industries with increasing internationalisation, such as the pharmaceutical industry, corporations today face the...
ISMS in a Nutshell - Part 3: Vulnerabilities, Threats, Risks
Information security is first and foremost about protecting your corporate assets. In our mini-series, we explain the terms, concepts and...
ISMS in a Nutshell - Part 2: The ISMS In the Company
Information security is first and foremost about protecting your corporate assets. In our mini-series, we explain terms, concepts and interesting...