The OWASP Top 10 is considered the global standard for web application security. It highlights the main risks and indicates where companies should pay closer attention. The current Top 10 for 2025 was presented last week at OWASP Global AppSec USA 2025 and makes it clear that conventional vulnerabilities such as SQL injection are becoming less significant. Instead, the focus is shifting to more complex attacks, for example in business logic, the software supply chain, or failure handling. As one of the few European companies, usd AG contributed the findings from our web application pentests, so that the OWASP Top 10 now not only reflect global trends, but also real vulnerabilities in the German market. A contribution that is entirely in the spirit of our mission: more security.
The OWASP Top 10 is an important indicator for us. It shows us the global development of vulnerabilities in web applications. But in our core market of Germany, we often recognize many of these developments earlier. Since we pentest a significant number of web applications every year, we have a clear picture of where threats are moving. That's why we actively participated this year, contributing our experience by anonymously donating our findings as data. Our goal is not only to reflect the list but also to help improve its practical relevance.
Matthias Göhring, Head of usd HeroLab

In this article, we present the key findings from the new OWASP Top 10, how the risk environment has changed, and what measures companies should take now.
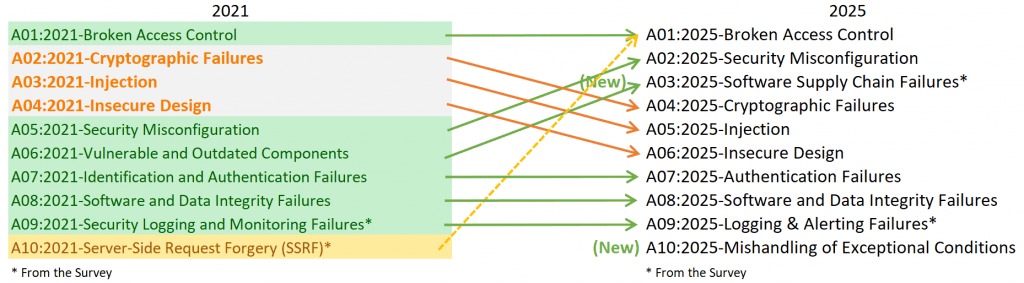
First place: Broken Access Control remains the undisputed leader
Broken access control refers to vulnerabilities where authorization checks are missing or faulty, allowing attackers to execute functions or view data for which they are not authorized. These continue to pose the greatest risk. Why? Because this category is strongly linked to the specific business logic of an application and is rarely prevented automatically by frameworks.
Common reasons:
- Unsecured API endpoints
- Transfer of sensitive data without authorization checks
- Incorrect assumptions about trustworthy clients
Our advice: Effective security needs a clear permission model and consistent authorization checks at all the right places. Automated tests only cover some areas, so manual checks and targeted pentests are a must.
Second place: Security Misconfiguration
From 5th place to 2nd place: Almost all applications offer configuration options to adapt them to individual requirements and environments, for example, to store your own certificates. Misconfigurations or certain combinations of settings can create vulnerabilities here, e.g., through unchanged default accounts or incorrectly set permissions in cloud environments.
Our advice: Rely on a recurring hardening process. Check whether the software manufacturers provide a hardening policy. This should also be used for verification purposes. In addition, remove unnecessary components and check configurations regularly, at least once a year manually.
New at 3rd place: Software supply chain failures
New to the ranking and straight in at number three: software supply chain failures. This category replaces the previous item “using vulnerable and outdated components” and broadens the view to include attacks on all parts of the software supply chain. These include compromised libraries in public package sources, manipulated build processes, and malicious code in external dependencies. The increase in these risks is directly attributable to real incidents in which supply chains were specifically used as a gateway for attacks.
Our advice: Use technical measures wisely, such as a complete software bill of materials (SBOM), automated scans of dependencies, code signing of your own artifacts, and strict isolation of the build environment from productive systems. Furthermore, you should continuously and automatically check whether newer versions with security patches are available for the libraries you use and update them promptly.
Injection vulnerabilities are decreasing – SQLi, SSTI, and XSS remain relevant
The injection category has fallen two places to fifth in the new ranking. This decline is primarily due to growing developer awareness and the use of modern frameworks that work with parameterization, automatic escaping, and input validation as standard. Nevertheless, three sub-forms remain present even in current projects:
- SQL Injection (SQLi): Occurs when unverified user input is inserted directly into SQL statements. It can be used to extract entire databases, manipulate data without authorization, or escalate further attacks. Modern ORMs automatically prevent SQLi in many cases; however, the risk remains high in legacy systems or with dynamically composed queries.
- Server-Side Template Injection (SSTI): A more modern risk that arises when template engines such as Jinja2, Twig, or Freemarker process unvalidated inputs. This allows attackers to execute code on the server side or query internal data. Applications in which developers enable advanced template functions or rely on insecure dynamic syntax are particularly vulnerable.
- Cross-site scripting (XSS): Targets the client and allows JavaScript to be executed in the victim's browser. Risks exist in particular with DOM-based XSS in complex single-page applications and with insufficient context encoding. Consequences range from session hijacking and data theft to UI manipulation.
Our experience from pentests shows: Injection vulnerabilities, including SQL injection, XSS, and SSTI, are generally encountered much less frequently today. Modern applications are usually well protected in this regard, as current frameworks and technologies prevent many of these attacks by default. The situation is different in older systems, where we still encounter these vulnerabilities much more frequently.
Newly added: Mishandling Exceptional Conditions
A completely new category is Mishandling Exceptional Conditions. OWASP summarizes 24 CWE classifications here, whose common denominator is unsafe or incorrect failure handling. Technical risks arise, for example, when detailed error messages reveal sensitive information, when exceptions bypass security checks unnoticed, or when security-relevant states are not reset correctly after an erroneous operation.
In practice, such problems often occur in combination with vulnerabilities in access control, for example when an exception triggers an alternative program path without authorization checks. The result: access to functions that should actually be protected.
Our advice: Develop effective countermeasures, such as a consistent and secure exception handling strategy, generic rather than detailed error messages, and targeted testing of errors and special cases.
Our conclusion on the OWASP Top 10: The focus is changing
(Source: OWASP Top 10)
The OWASP Top 10 in 2025 shows that technical advances have reduced classic vulnerabilities. However, new risks arise where processes are more complex and less standardized. Implementing access controls requires the development of a consistent authorization concept and full implementation. Since mistakes often occur here, broken access control remains in first place. SQLi is on the decline, while SSTI and XSS remain as relevant as ever in modern, dynamic applications. Supply chain failures highlight the impact of external components and processes on security, while mishandling exceptional conditions raises awareness of the importance of robust error handling.
For developers and security teams, this means that in addition to classic input validation, business logic, supply chains, and exception handling must be addressed equally. Security should not be understood as a matter of individual functions or framework measures, but as a continuous quality process - with regular pentests, clear guidelines, and a willingness to check even inconspicuous paths for vulnerabilities.



