The Payment Application Data Security Standard (PA-DSS), the PCI Security Standards Council’s current security standard for payment software will be completely replaced by its successor, the Secure Software Standard, in October 2022. Together with the Secure Software Lifecycle (Secure SLC) standard, this forms the Council’s new PCI Software Security Framework. Certification according to the two new standards has been possible in parallel to PA-DSS since last year.
This transition phase is a good time for affected companies to address the most important questions: What impact will the new Secure Software Standard have on future certifications? Which deadlines should be kept in mind? How can you prepare for the replacement and the new certification in the best possible way and in good time?
Greater Software Siversity and More Flexibility
The requirements of the two standards PA-DSS and Secure Software Standard cannot be compared 1:1. The Secure Software Standard supports a broader range of applications, architectures and functions of software than the PA-DSS. It also brings more agility with regard to current development techniques and release cycles, which can, for example, create more transparency when updating software products.
In contrast to the PA-DSS, the Secure Software Standard also formulates target-oriented requirements whose concrete implementation software manufacturers can define themselves. This gives companies greater flexibility in the implementation of their security measures.
Another significant advantage of the Secure Software Standard is the possibility for software manufacturers to be additionally certified according to the Secure Software Lifecycle Standard. In this case, the development processes of the manufacturer itself are certified, so that it can check minor changes to its software itself for compliance with the Secure Software Standard.
Modules with Requirements for Specific Software Products
The Secure Software Standard has a modular structure. Each module contains a set of requirements that address specific use cases. At this time, the PCI Council has published 2 modules: the “Core” module with general security requirements for all payment software products, and the “Account Data Protection” module, which includes specific requirements for payment software that stores, processes, or transmits cardholder data or sensitive authentication data.
As a third module, the Council has announced the publication of the “Terminal Software” module. This contains a set of requirements for the use and operation of purpose-built payment terminals.
The modular design makes the Secure Software Standard much more dynamic and adaptable for updates and changes in view of future developments in practice.
Important Key Data in the Transition Phase
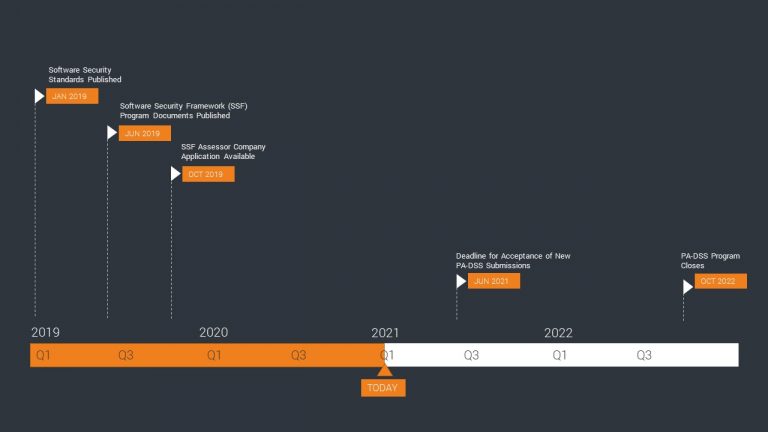
To ease the transition process for all parties involved, a transition period has been provided by the PCI Council during which PA-DSS will remain available. Affected organizations should keep the following two dates in mind: June 2021 and October 2022.
At the moment, re-certifications according to PA-DSS and submissions of new payment applications for certification according to PA-DSS are still possible. This will change on June 30, 2021, after which newly submitted payment applications must be certified directly according to the new Secure Software Standard.
The PA-DSS will expire in October 2022. Existing PA-DSS-validated applications will remain on the list of validated payment applications until their expiration date. Through the familiar process, providers can also submit changes to these applications until October 2022. After that, the applications will be listed under the “Acceptable Only for Pre-Existing Deployments” category in the list of certified applications maintained by the Council.
Own illustration based on illustration of the PCI Security Standards Council
( Source: https://blog.pcisecuritystandards.org/how-to-successfully-transition-software-from-pa-dss-to-the-pci-secure-software-standard )
Workshop and Gap Analysis as First Steps of Preparation
The question for companies now is how they can best prepare for the changeover. As a first step, our certified experts recommend a workshop in which the new framework, the standards and the requirements are presented. Based on this, a gap analysis between the PA-DSS and the Secure Software Standard should be performed for all relevant software products. This will give companies a meaningful idea of the requirements of the new standard and how they can prepare for a future audit in accordance with the Secure Software Standard.
Our expert Torsten Schlotmann talked about the changes, some of which are significant, that await you and the advantages that an additional certification according to the Secure SLC Standard can have for you.
Do you have questions about the Secure Software Standard or need assistance with the transition? Get in touch, we are happy to help.



