NIS-2
Is Your Company Affected by the EU Directive?
The NIS-2 Directive
Are we affected? What requirements do we have to implement? How much time do we have to do this?
The NIS-2 Directive (Network and Information Security 2, NIS-2) is currently causing question marks for many companies in Europe. This is because with the new directive, the EU is focusing its cyber security offensive on other "essential and important facilities" in addition to critical infrastructures.
The EU directive will be transposed into national law by October 2024 and will then be binding for affected companies. We can provide you with advice and support in preparing for and implementing the requirements.
Requirements
Companies affected by NIS-2 are obliged to operate a verifiable information security management system (ISMS). Based on this, they must take appropriate technical, operational and organizational measures to control cyber security risks, prevent security incidents and minimize potential impacts. The requirements of NIS-2 apply to the entire company, not just to individual systems classified as critical.
Timeline
NIS-2 was published on December 27, 2022 and came into force on January 16, 2023. The EU member states are currently transposing the requirements of NIS-2 into national law. This transition must be completed by October 2024. Even if it can be assumed that a reasonable transition period will be granted for implementation after this date, we strongly recommend that you prepare early.
Scope
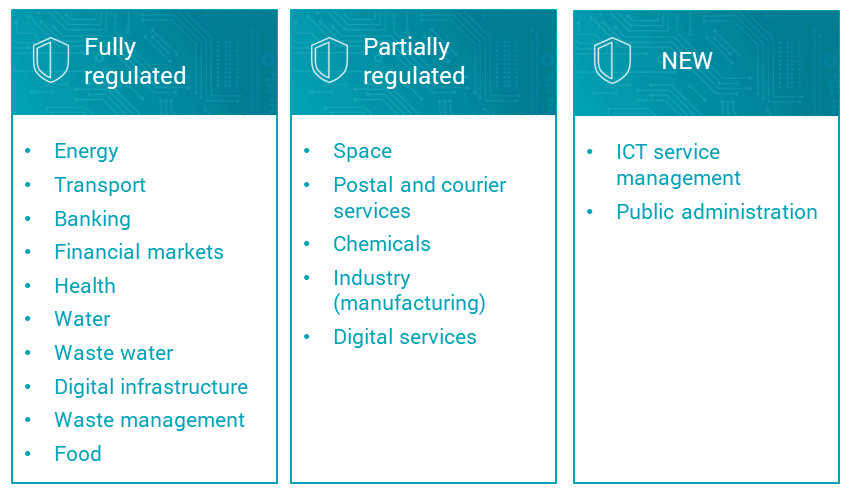
The NIS 2 Directive covers 18 sectors that are of crucial importance to the economy and society. It applies to companies with 50 or more employees and a turnover of 10 million euros. Some of the 18 sectors are already fully or partially regulated by existing legislation in Germany, while others are new:
How to prepare
Start your preparations for NIS-2 with a Gap Analysis in your company. Regardless of whether you are already having KRITIS audits carried out on the basis of the IT Security Act or are only coming within the scope of NIS-2: With the help of a Gap Analysis, you can uncover specific deviations in your company's security organization. This allows you to plan and implement suitable implementation projects in good time.
We are at your side
We are here for you. Following the Gap Analysis, we will of course be on hand to advise you and support you in implementing the NIS 2 requirements.
Are you currently planning to set up an ISMS in accordance with ISO 27001 or are you already in the process? If so, we recommend combining your ISMS project with a closer look at the NIS-2 requirements. We will be happy to help.

Vinzent Ratermann
Expert for the IT Security of Critical Infrastructures
A NIS-2 implementation project usually involves extensive human and financial resources. We therefore advise you to make the most of the time remaining until October 2024. Together with our experienced consultants and security auditors, take an early look at the requirements of NIS-2 and identify any deviations in your company.
More Insights on NIS-2
NIS-2 and DORA: Why Two Pieces of EU Cybersecurity Legislation?
Ready for NIS-2? How to Prepare Your Company
