The Digital Operational Resilience Act (DORA) will apply as of January 17, 2025. In addition to routine operational resilience testing, DORA will also make it mandatory for certain financial companies to carry out threat-led penetration testing (TLPT) every three years.
The detailed DORA requirements for TLPT are set out in regulatory technical standards (RTS) and implementation standards (ITS) and are therefore not yet fully defined. In this article, we share with you what we already know from the draft of the RTS/ITS published at the end of 2023 and answer the most important questions:
- What is TLPT?
- Who is required to carry out TLPT?
- What parties are involved in TLPT?
- What is the TLPT process?
- Is TLPT under DORA the same as TIBER-DE?
- How can I start preparing for TLPT?
- What do we know and what comes next?
What is TLPT?
Threat-Led Penetration Testing is an extended form of Red Teaming, which is used to test the resilience and security of critical and important functions in financial companies.
'Threat-led penetration testing (TLPT)' means a framework that mimics the tactics, techniques and procedures of real life threat actors perceived as posing a genuine cyber threat, that delivers a controlled, bespoke, intelligence-led (red team) test of the financial entity's critical live production systems.
DORA, Article 3 (17)
Before the actual test phase, TLPT carries out a threat analysis (threat intelligence) in which information is collected on relevant current, industry- and company-specific threats. Based on this, realistic attack scenarios are defined in which various attack surfaces such as physical attacks, social engineering and technical attack vectors are covered. These attack scenarios are then carried out as Red Team Assessments. The focus is on testing the production systems as realistically as possible.
TLPT thus differs from classic penetration tests, which are generally optimized for a comprehensive test coverage of individual assets. DORA calls for the implementation of TLPT as a complementary means to classic, asset-based penetration tests, not as a replacement.
Who is required to carry out TLPT?
Not all financial institutions affected by DORA are automatically obliged to carry out TLPT. Competent national supervisory authorities (in Germany BaFin) or the ECB identify those companies that must carry out TLPT and inform them of their obligation.
For identification purposes, the respective authority takes into account the proportionality principle and the following additional criteria:
- impact-related factors, including in particular the extent to which the services and activities provided by the financial undertaking have an impact on the financial sector;
- financial stability concerns, including the systemic character;
- the risk profile, the ICT maturity of the financial entity or relevant technology features.
Source: RTS Draft on TLPT, Article 3.4(24)
External third-party providers of these financial institutions must also be included in the scope of testing if they operate or provide IT systems or applications that support a critical or important function for the financial company. To this end, this financial company must contractually ensure that the relevant third-party providers participate in the implementation of a TLPT.
What parties are involved in TLPT?
TLPT Cyber Team (TCT)
In Germany, the TLPT Cyber Team is based at the Deutsche Bundesbank and supports financial institutions in carrying out a TLPT. In addition, the TCT certifies the correct execution of the test after its completion. BaFin takes on a supervisory role and is consulted on certain parts of the test.
Control Team (CT)
The Control Team takes on a coordinating role within the tested company. It manages the implementation of the entire TLPT. Its tasks include risk management, the operational management of test activities and the selection of external providers.
Blue Team
The Blue Team is the internal company team that monitors the IT security of the IT infrastructure operationally and implements counter measures in the event of a cyberattack.
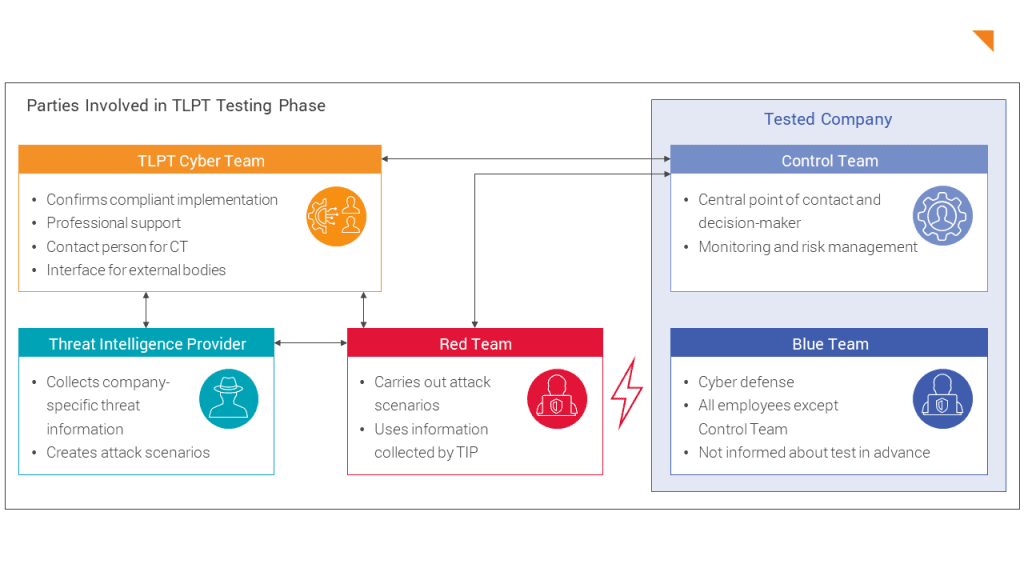
Threat Intelligence Provider (TIP)
The Threat Intelligence Provider provides the general, industry-specific and company-specific threat information. It is mandatory that this is an external provider.
Red Team Provider (RTP)
The Red Team Provider provides the team to carry out the security assessment.
The guideline for TLPT contains requirements for TIP and RTP, which the commissioning company must observe. These include relevant certifications, proven industry expertise and experience from similar projects that have already been completed. To simplify the selection process, Threat Intelligence and Red Team can be provided by the same external provider, provided that a separation of personnel can be guaranteed.
What is the TLPT process?
The TLPT is initiated by the company carrying out the project together with the TLPT Cyber Team of the Deutsche Bundesbank and, if applicable, BaFin. During implementation, a project goes through three phases, which are summarized below:
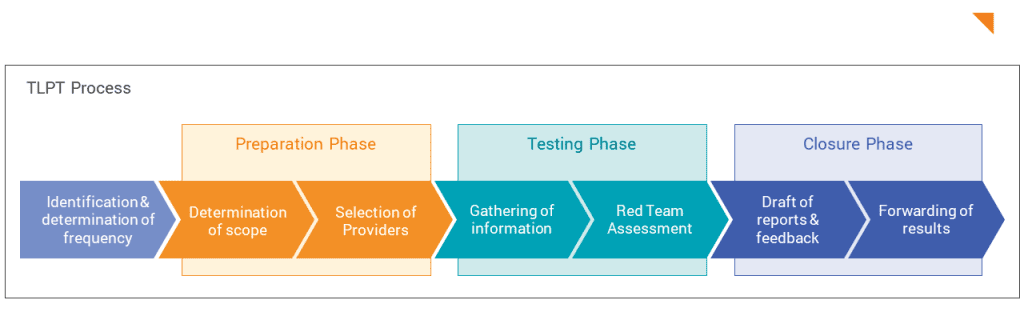
Preparation Phase
A report on the national threat situation from the Deutsche Bundesbank, which contains current and general information on threats in the financial sector, serves as the basis for initiation and preparation. In addition, the financial company to be tested determines the scope of the test and defines an initial draft of targets (flags) for the RTP, which are refined and updated as the test progresses.
Two documents emerge from these first steps: a project plan and a scope specification.
The scope specification is submitted to the competent supervisory authority. Any comments can be submitted by the TCT. Towards the end of the preparation phase, the (external) Threat Intelligence and Red Team Providers are involved and informed about the project plan and the planned scope.
Testing Phase
At the start of the testing phase, the TIP determines the company-specific threat situation and drafts a report based on the report on the national threat situation and internal company information provided in advance. The result of the TIP's work is a report on the company-specific threat situation, in which concrete attack scenarios are proposed for the RTP. At least three suitable attack scenarios are selected to be carried out by the RTP. The RTP then plans the actual test implementation and creates a test plan, which must be approved by the Control Team and the TLPT Cyber team. These two preparatory tasks should take up around a third of the testing phase.
The main part of the testing phase, which lasts at least 12 weeks, is the actual assessment carried out by the RTP. During this active testing phase, the RTP executes the defined attack scenarios. In doing so, vulnerabilities are identified and exploited in order to achieve the flags defined in advance. During the entire active testing phase, the RTP testers are in contact with the Control Team and, if necessary, the TLPT Cyber Team and report on the progress made. The TIP is available for additional advice at the request of the Control Team and provides further threat information as required. If necessary, the RTP will adjust the execution of its tests based on this new information.
Closure Phase
The first stage of the closure phase is the preparation of the results reports. The RTP test report records the identified vulnerabilities. In addition, the Blue Team's test report documents the attack attempts it detected and any counter measures taken. DORA requires that Red and Blue Team results be discussed together to discuss defense improvements.
The results are incorporated into a final report prepared by the financial company. This contains, among other things, a remediation plan that includes the necessary measures to improve security and a timetable for their implementation. However, technical details on vulnerabilities are not included. The final report must be submitted to the Deutsche Bundesbank to confirm the proper implementation of the TLPT.
Is TLPT under DORA the same as TIBER-DE?
If you are already familiar with the TIBER-DE framework, you will recognize many of the processes and parties described above, as the requirements and processes of TLPT under DORA are largely based on TIBER-DE.
In contrast to TIBER-DE, which is completely voluntary for companies, DORA obliges certain financial companies to carry out TLPT as a supervisory measure.
Another important difference lies in the recognition of internal testers: While TIBER-DE excludes the use of internal testers, DORA allows them under certain conditions. There are also minor differences in the implementation itself: For example, the final discussion of the results between the external Red Team and the company's internal Blue Team is mandatory under DORA, while TIBER-DE only recommends it.
As an affected company, how can I prepare for TLPT now?
Are you expecting to be asked to carry out a TLPT by your competent supervisory authority? Take preparatory measures now that will be helpful for a smooth and efficient implementation later on.
Definition of critical or important functions
A central requirement of DORA, which is also essential for a TLPT, is the definition of critical or important functions and the associated assets in your company. An overview of these assets is already required in the first step, the scope specification for the TLPT.
Integration into the central monitoring solution
Ensure that all assets defined in the previous step are integrated into your central monitoring solution (SIEM) and are actively monitored.
Agreements with relevant third-party providers
It is a good idea to approach relevant third-party providers who will most likely have to participate in a TLPT at an early stage. If this has not yet been done, existing and upcoming contracts should be adapted to oblige relevant third-party providers to participate in a TLPT.
Proactive smaller Red Team Assessments
Selectively, smaller Red Team Assessments can also help in advance to subject defensive measures to an initial test. These assessments can be carried out with a reduced scope and independently of a TLPT. In addition to the technical aspects, they can help all stakeholders involved to become familiar with important key aspects of the scope determination, preparation and implementation of an assessment and to incorporate them into the first TLPT.
For third-party providers: Bundling of required TLPT
Third-party providers can also make preparations in advance. If a service that supports critical or important functions is offered to several financial companies, it helps to identify all affected customers as early as possible. DORA offers the option of bundling several TLPTs with one service provider if the same service is provided for different customers. This is intended to avoid duplicate tests and to save time and effort.
Summary: What do we know at this time?
DORA requires large financial companies to carry out a Threat-Led Penetration Test (TLPT) every three years. The test focuses on all systems that support critical or important functions of the company. This includes services provided by third-party providers. If you need to carry out a TLPT, it is worth identifying the affected systems and service providers now and ensuring that contracts include participation in a TLPT. In addition to the financial company and the relevant third-party providers, other parties are involved. These include the TLPT Cyber Team, based at the Deutsche Bundesbank, as well as providers for Red Teaming (RTP) and Threat Intelligence (TIP).
Outlook
DORA will become fully applicable in January 2025. Details on the design of TLPT can be found in the draft version of the RTS from November 2023. The final version is expected to be released in mid-2024. In any case, it is worth keeping up to date with the final version of the RTS and any upcoming changes. We will of course continue to inform you about all developments in our news blog.
Would you like to prepare for TLPT with proactive smaller Red Team Assessments or do you need help preparing for DORA?



